- Can't be uninstalled via Control Panel
- Installs itself without permissions
- Connects to the internet without permission
- Slow internet connection
- Slow Computer
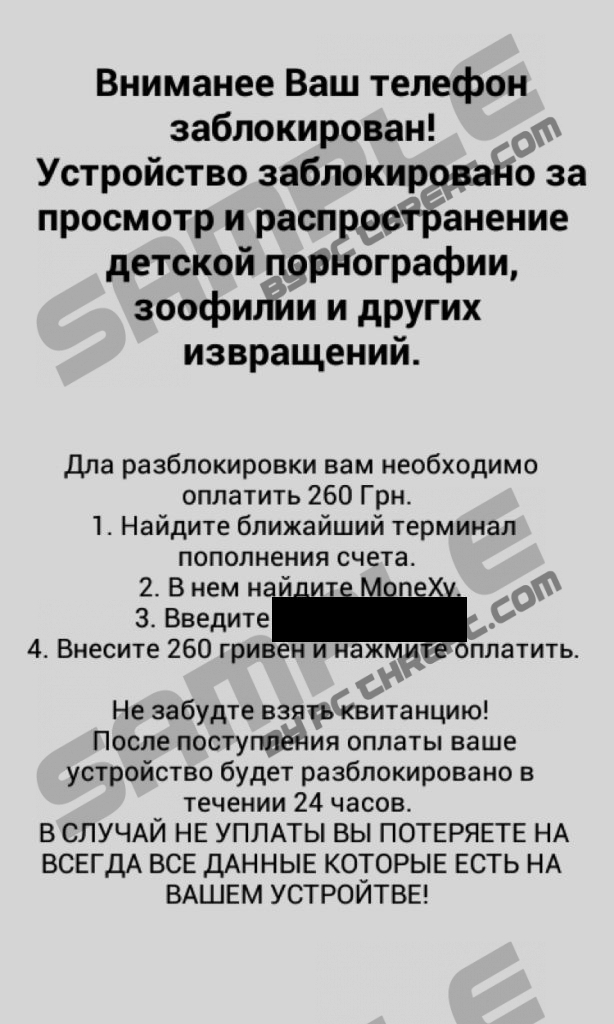
Android ransomware virusThe Windows OS is not the only platform targeted by cyber crooks; the Android OS has already been affected by the Android-based ransomware viruses, some of which cannot be removed from mobile devices. The latest ransomware infection is called Simplelocker and is known to be spread in Ukraine and Slovakia, and the deceptive warning displayed by the threat is writing in the Russian language. The android ransomware virus scans the data stored on a SD card inserted in the mobile device and encrypts files with extensions such as .jpg, .jpeg, .png, .doc, .txt, .mp4, and some others. The user of the infected tablets and smart phones is provided with a warning claiming that his/her device is locked because of his/her illegal activities, such as the use and distribution of child pornography and zoophilia. More important, the user is instructed to pay 260 hryvnias, which is roughly $22, using the Ukranian MoneXy money transaction system. As the ransom warning suggests, the encrypted data will be unlocked with 24 hours; however, the user should not pay up because there is no guarantee that the cyber attackers will enable access to the data encrypted. The removal of the android randonsomware virus is impossible because the infection does not have the functionality of file decryption. All that you should do is take measures to prevent the infiltration of the Simplelocker and other malicious programs. The android ransomware virus Simplelocker, also known as Simplelocker.A, is not the only Android-based ransomware infection. For example, there is ransomware for Android devices called Koler, which is very similar to the infamous Reveton malware which has caused a lot of damage to Windows OS users. The Koler malware is referred to as policeware or police locker because the notification displayed by the infection features the logos and the names of famous law enforcement institutions. The Koler ransomware infection is known to have tricked victims in the United Arab Emirates, UK, Germany, USA, Italy, and Poland. This android ransomware virus preserves your files intact and can alter the content of the warning depending on your geographical location. In the case of the America-based version of the Koler virus, the computer user is warned that he/she is dealing U.S.A Cyber Crime Center and FBI Department of Defense. Unlike the Simlelocker ransomware infection, Koler displays its fraudulent warning once you close it which makes it impossible to get to the Settings, where you could remove the malware. The reboot of the program is ineffective because the ransomware warning pop-ups shortly after the restart. You can remove this android ransomware virus by restoring factory settings, which erases all your data stored on the device. The Koler virus is not available on the Google Play, thus, in order to get this android ransomware infection on the computer, you need to have the Allow installation of apps form unknown sources option selected. It is highly inadvisable to install programs provided not from the OS-related software distributors because it may lead to adverse consequences. You should keep away from untrustworthy applications and questionable sources and backup your data regularly. Some security tool may also come in handy, but bear in mind that the android ransomware is not the only threat that can afflict your mobile device. As well as the Windows operating systems, the Android is also targeted by the developers of fake security programs, whose goal is to extort money from unsuspecting users. If you do not want to pay a heavy price for your carelessness, start making some changes right now. How to restore Android factory settings
Keep in mind that by restoring factory settings you lose your data stored on the device. |
|
Download Spyware Removal Tool to Remove*
Android ransomware virus
|

|


Post comment — WE NEED YOUR OPINION!