- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Abnormality CheckerWindows Abnormality Checker is a fake program created by the black hat hackers who seek to steal money from the Windows users. Windows Abnormality Checker belongs to the Rogue.VirusDoctor family, which includes such latent programs as Windows Advanced User Patch, Windows Internet Booster and many others. Windows Abnormality Checker deceives the user about the system’s security; thus, this application should be removed at once. If you find suspicious balloon warnings in the right corner of the screen and different threats presented by Windows Abnormality Checker, ignore this information, because it is a lie. The annoying pop-ups saying that the system is no longer immune to the Internet threats are simulated. Moreover, the threats such as P2P-Worm.Win32 and Roorkit.Win32.KernelBot presented by Windows Abnormality Checker should be ignored. These threats do exist, but if the system is infected with Windows Abnormality Checker, these names do not mean anything. Moreover, Windows Abnormality Checker will produce warnings and errors which should be also ignored: Error Warning! Virus Detected According to the first error given, you should active Windows Abnormality Checker so that it can run a full system scan and, as a result, delete the threats. However, it is impossible, because the threats are nonexistent in the system, and the activated version of Windows Abnormality Checker is just incapable or removing anything for the only reason – it was created to scare people. Therefore, you should not reveal your financial data such as bank account number, CVV or passwords, because everything will be recorded the criminals. A great deed would be to get rid of this infection, and you can do it manually after entering an activation or registration key: 0W000-000B0-00T00-E0020 The key makes Windows Abnormality Checker act as if has been activated after the purchase; therefore, certain processes of the system which are necessary to be accessed, are available to the user. After the registration of Windows Abnormality Checker, the Internet connection is restored as well as the Registry Editor. Moreover, the user can watch The Task Manager, which was hidden, and see what processes are running in the system. All in all, when the Registry is restored, the user might proceed with the removal of the rogue. The components of Windows Abnormality Checker have to found and delete from the system. None of them can be left in order to prevent the regeneration of Windows Abnormality Checker or another infection. Specific registry entries, files and processes have to be terminated. If you are a user which uses a computer on a daily basis to satisfy basic needs such as to check the mail or “like” a picture on Facebook, do not attempt to remove Windows Abnormality Checker on your own. In such a case, the best option for removal of Windows Abnormality Checker is using a trusted antispyware application which is capable of delete the rogue and protecting the system from infections.
Download Spyware Removal Tool to Remove* Windows Abnormality Checker
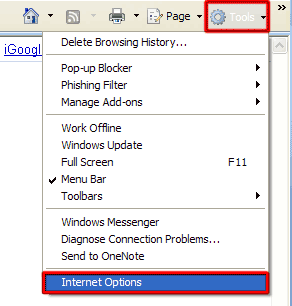
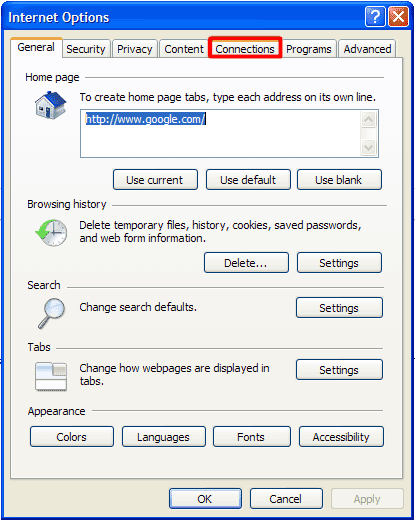
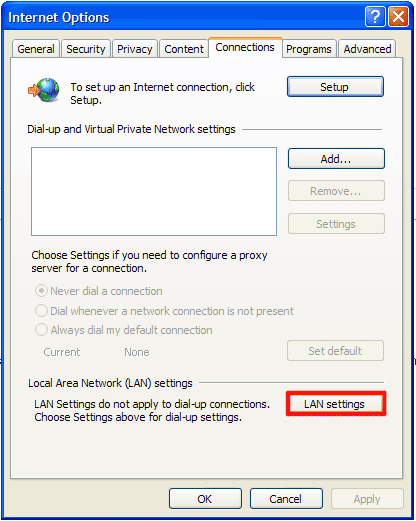
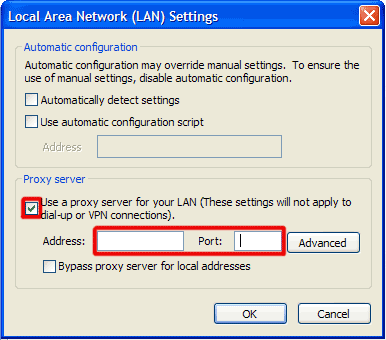
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Abnormality Checker
| ||||||||

|
How to manually remove Windows Abnormality Checker
Files associated with Windows Abnormality Checker infection:
%AppData%\Protector-[Random].exe
%AppData%\W34r34mt5h21ef.dat
%AppData%\result.db
%CommonStartMenu%\Programs\Windows Abnormality Checker.lnk
%Desktop%\Windows Abnormality Checker.lnk
Windows Abnormality Checker DLL's to remove:
Windows Abnormality Checker processes to kill:
Remove Windows Abnormality Checker registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Win
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-5-6_2"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "ungklgkqft"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alertsvc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\belt.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\iface.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\netspyhunter-1.2.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rscdwld.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tcm.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winstart.exe

Post comment — WE NEED YOUR OPINION!