- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Safety SeriesYou should use an appropriate computer security application to protect your data properly. Windows Safety Series is one of fraudulent applications which should not be regarded as suitable for the protection, because it is a computer infection with an interface of Windows applications. Because of its appealing characteristics, the malware is often mistaken for a legitimate application; however, it belongs to the Rogue.VirusDoctor family that consists of the rogue’s predecessors such as Windows Secure Workstation, Windows Anti-Malware Patch, Windows Virtual Security and many others. As a clone of the malicious applications, Windows Safety Series applies the same scare tactics to deceive Windows users into considering the possibility of buying its non-functional full version, which is, of course, presented as the best product to remove such “threats” as Trojan.Win.32.Qhost, Virus.Win32, Sality, Adware.Win32.BHO and many others. If you think that you can save money and delete the threats on your own, you are wrong, because they do not exist in the system. Hence, you should also ignore such bogus notifications as given below: Error Error Error Besides receiving simulated notifications, you will also find some malfunctions of the system’s performance. Access to the Internet and some Windows applications will be disabled, not to mention the fact that the registry, where many changes regarding the performance of the machine are done, and Task Manager are inaccessible, as well. Non-responsiveness of some parts of the system and lack of access to the Internet are the most noticeable features which are supposed to be regarded as the consequences of having “dangerous” infections. The sooner you remove Windows Safety Series, the sooner the system starts returns to its former condition. To make the removal of Windows Safety Series easier, copy and paste the activation key provided below to an activation box and register the rogue so that no annoying scans and misleading warnings are displayed. Moreover, if you want to delete the rogue manually, you will manage to access the registry and delete irrelevant registry entries. Do not forget to delete the rogue-related files and processes to fully remove Windows Safety Series. If you see that the manual removal of this mean application is too confusing, after having activated the malware, download a reliable antispyware application to delete the infection automatically. The application will detect and terminate the infection, and the only thing that you will have to do afterwards is to repeat the scanning regularly to make sure that the system is secure. Activation key: 0W000-000B0-00T00-E0020
Download Spyware Removal Tool to Remove* Windows Safety Series
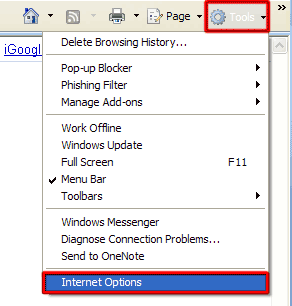
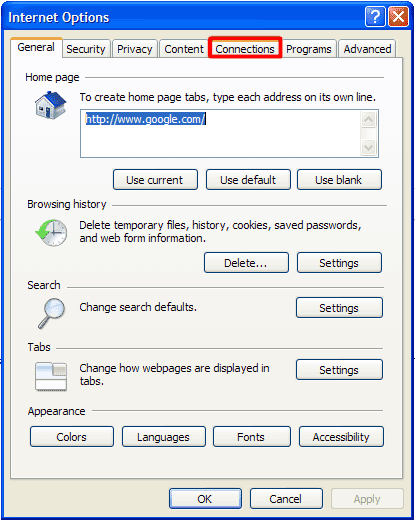
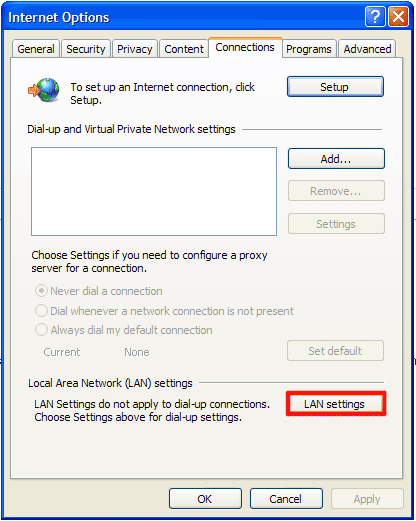
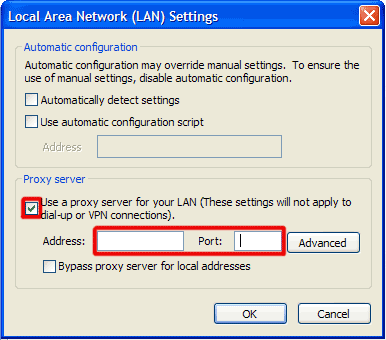
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Safety Series
| ||||||||

|
How to manually remove Windows Safety Series
Files associated with Windows Safety Series infection:
%AppData%\Protector-[Random].exe
%AppData%\result.db
%AppData%\1st$0l3th1s.cnf
%CommonStartMenu%\Programs\Windows Safety Series.lnk
%Desktop%\Windows Safety Series.lnk
Windows Safety Series DLL's to remove:
Windows Safety Series processes to kill:
Remove Windows Safety Series registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "otbpxlqhjd"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmdagent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[1].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npfmessenger.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsadbot.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe

Post comment — WE NEED YOUR OPINION!