- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Shows commercial adverts
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Secure WorkstationDo you think that Advanced Windows Security Center is a legitimate application? Well, it is not, and if you notice this application on your screen claiming that its simulated licensed version needs to be enabled within your system, you need to recognize that this is just a trick to make you think that supposedly authentic Windows’ attribute is essential for full system’s protection. Windows Secure Workstation, clone of Windows Virtual Security, is a fictitious antispyware which might employ other seemingly useful attributes like mimicked Firewall or Automatic Updates to fool you into thinking that it has been developed by Microsoft. This, of course, is not true, and you should know that any respectable company would never breach your system’s security and offer you to purchase its full version products. You need to remove Windows Secure Workstation from your system, because this illegitimate security tool is managed by schemers, and they will not miss a chance to trick you into submitting at least $49.95! If you think you could find an authentic company offering legitimate lifetime protection services for this price, you are very wrong, and cyber criminals can only offer this price, because their bogus product will never delete infections from your system. If you want authentic malware removal products, you need to trust reliable, legal software, and ignore products which can only trick you into wasting your money. Various security notifications (below) can really do a good job at tricking you, because these will not differ from other regular Task Bar notifications. Warning! Spambot detected! Error All information declared is bogus, and if you choose to trust any recommendations to remove malware or enable protection, you will be forwarded to the rogue’s purchase page. Ignore this source by all means, as this is the last step for crooks to fool your money out of you! What you should do with all information declared by the fictitious Windows Secure Workstation program is remove it mercilessly, and you can do that with special activation code’s registration: 0W000-000B0-00T00-E0020. What is more, this key will help you restore removed access to Task Manager, Registry Editor, and blocked running of most executables. This implementation should also help with any Internet connection issues; however, if these prevail, you are welcome to use our Internet connection renewal instructions. The activation key will not delete Windows Secure Workstation, but will definitely alleviate both manual and automatic removal operations. Those, who know how to find and delete malignant files using Task Manager and Registry Editor tools, will be able to remove Windows Secure Workstation virus manually, but if you are not sure how to identify authentic and malignant elements – automatic removal is the way to go.
Download Spyware Removal Tool to Remove* Windows Secure Workstation
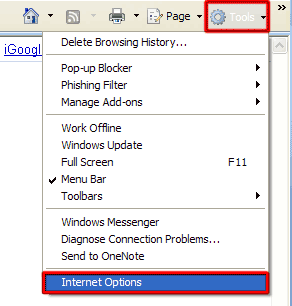
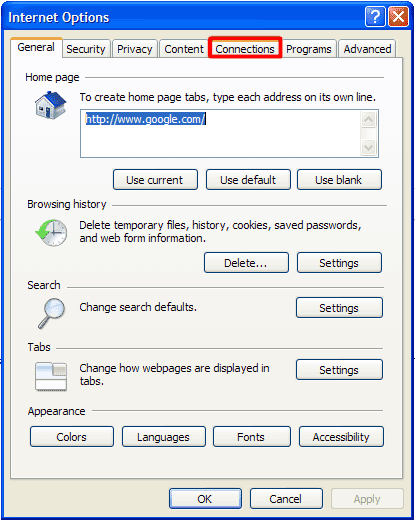
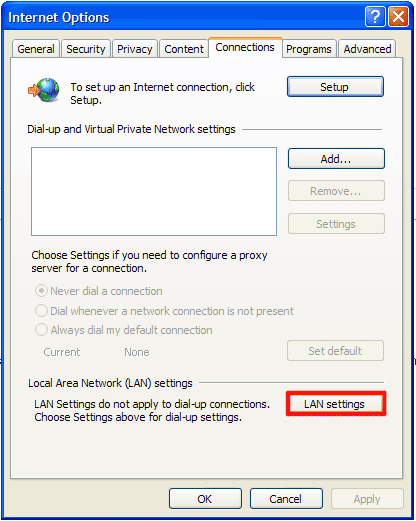
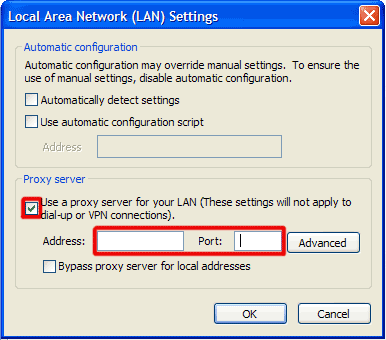
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Secure Workstation
| ||||||||

|
How to manually remove Windows Secure Workstation
Files associated with Windows Secure Workstation infection:
%AppData%\Protector-[Random].exe
%AppData%\result.db
%AppData%\1st$0l3th1s.cnf
%CommonStartMenu%\Programs\Windows Secure Workstation.lnk
%Desktop%\Windows Secure Workstation.lnk
Windows Secure Workstation DLL's to remove:
Windows Secure Workstation processes to kill:
Remove Windows Secure Workstation registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "otbpxlqhjd"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmdagent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[1].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npfmessenger.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsadbot.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe

Post comment — WE NEED YOUR OPINION!