- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Changes background
- Connects to the internet without permission
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Active GuardWindows Active Guard is a computer infection having an interface and characteristics of antivirus software. This application is an exact copy of Windows Security Renewal, Windows Home Patron and other fraudulent applications composing the Rogue.VirusDoctor family. The malware is created to get your money by making you believe that you have to acquire a full version of Windows Active Guard which supposedly removes infections. Various scare tactics are employed to persuade you into believing that the system is jammed with infections of different levels of danger. The information provided by the malware should be ignored, because it does not present the real situation. It is highly advisable to remove Windows Active Guard as soon as it is noticed on the computer. If the rogue is not deleted, the computer cannot function effectively due to the impairments produced by the infection. You might start truly believing that you lost access to the Internet due to the presence of infections, which are constantly detected by the malware. The rogue disables certain executable files and wants you to think that those infections are so dangerous that they can disturb the running of the system. Task Manager and Registry Editor, where many new registry entries are created, are hidden as well so that you cannot delete the malware manually. Most importantly, as Windows Active Guard pretends to operate as a security tool, it presents many imaginary threats, which are the results of constant simulated scans. Such infections as P2P-Worm.Win32, Virus.Win32Sality etc should not be taken into account because they do not exist in the system, and you should not try to delete them manually, because accidentally you might delete legal system files. Hence, removed the very infection, and you will not have to worry about “infections”. You should also pay no attention to false warnings saying that you are at risk. Some messages are presented: Error Error Error If you want to get rid of these pop-ups, restore the Internet and again use the computer properly, use this activation key to register the rogue 0W000-000B0-00T00-E0020. This key is the same you would get after the exposure of your identifiable data to the criminals who would use the information to rob you. After activating Windows Active Guard, you can delete it without disturbance of cunning pop-up messages. If you want our expert advice about the removal of Windows Active Guard, use a reputable and powerful antispyware tool to delete the rogue, because if the rogue is deleted in this way, the chance of a full recovery of the infection is minimized to zero. Another advantage of using an automatic spyware removal tool is that you can use it regularly to check whether or not the system is at risk. Rescanning of the system will help to maintain your system’s security, and you will not have to worry about all types of infections and how they affect the system’s functioning.
Download Spyware Removal Tool to Remove* Windows Active Guard
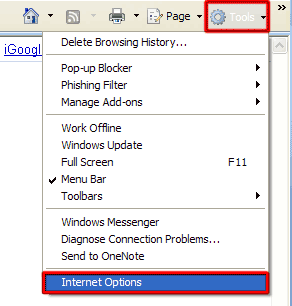
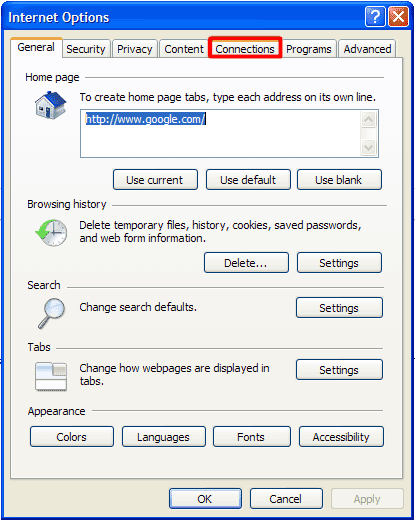
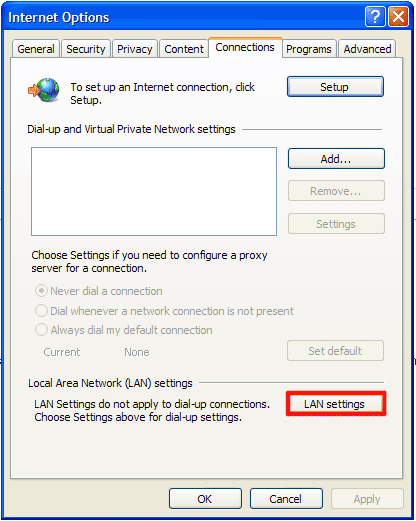
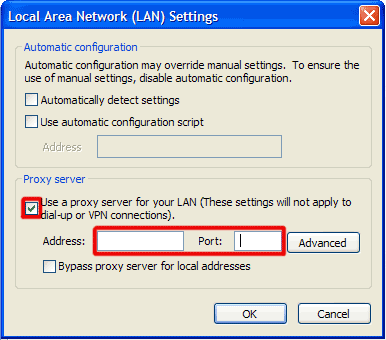
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Active Guard
| ||||||||

|
How to manually remove Windows Active Guard
Files associated with Windows Active Guard infection:
%AppData%\Protector-[Random].exe
%AppData%\result.db
%AppData%\1st$0l3th1s.cnf
%CommonStartMenu%\Programs\Windows Active Guard.lnk
%Desktop%\Windows Active Guard.lnk
Windows Active Guard DLL's to remove:
Windows Active Guard processes to kill:
Remove Windows Active Guard registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "otbpxlqhjd"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmdagent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[1].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npfmessenger.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsadbot.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe

Post comment — WE NEED YOUR OPINION!