- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Annoying Pop-up's
- Slow Computer
Windows Secure Web PatchThe Rogue.VirusDoctor family is expanding rapidly, because another bogus application called Windows Secure Web Patch has been produced. This bogus software is a clone of such deceptive software as Windows Instant Scanner, Windows Privacy Counsel and others, which are identical and work according to the same scheme. Windows Secure Web Patch should not be installed on the computer, because, as soon as the infections invades the system, certain modifications are made to make users think that their computers have been infected with threats. If you have ever thought of downloading or using this bogus application for the protection of your computer, forget about it because Windows Secure Web Patch is not antivirus software, and if you already have it on your computer, delete it at once. Windows Secure Web Patch gets into the system unnoticed unless it is installed by a user. As soon as it puts down it roots in the system, the systems starts functioning according to the rules of the rogue. The Internet connection becomes no longer available, because the rogue disables it so that a removal tool cannot be downloaded. Certain executable files which are normally used to detect infections are disabled by registry entries created in Registry Editor which is hidden, as well. Moreover, the malware hides Task Manager so that the processes that are running in the system are not visible. In addition to the malfunctioning of the system, Windows Secure Web Patch produces numerous scans of the system to deceive users about the system’s security. The bogus scans usually end with a list of imaginary infections which should not be attempted to be removed manually, because they do not exist in the system. The same and other infections are also presented in a form of notifications, which can pop up out of Task Bar or unexpectedly appear on the screen. Some misleading notifications are presented: Error Error Error If you follow the rogue’s instructions to activate it, which, in return, removes “infections”, you will throw your money away, because a purchase of the malware is useless. Such financial details as credit card number, login passwords, CVV, etc and your money are the goal or cyber criminals. If you really want to get rid of infections, remove Windows Secure Web Patch from the computer, because this malware might be the only infection in your system. The removal of Windows Secure Web Patch can be eased if it is activated with this activation key: 0W000-000B0-00T00-E0020 After the activation, detect and delete the elements of Windows Secure Web Patch so that the infection does not regenerate. If there is something related to the rogue left in the system, the infection will reappear. As this way of removal is recommended only for experienced Windows users, it is much better to remove Windows Secure Web Patch by using an authoritative removal tool which is capable of eliminating malware from the system. Only this way of deletion ensures that the rogue is fully removed and that the infection will not be revived.
Download Spyware Removal Tool to Remove* Windows Secure Web Patch
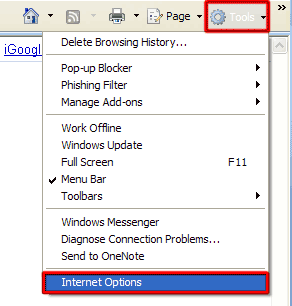
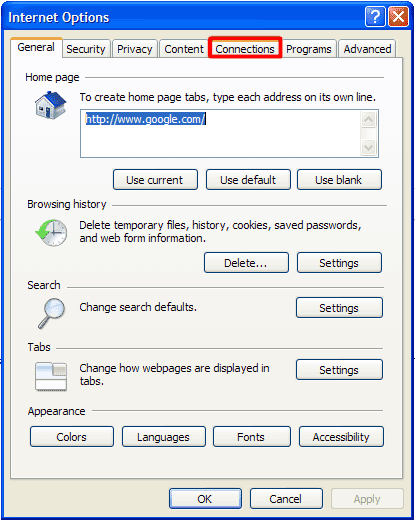
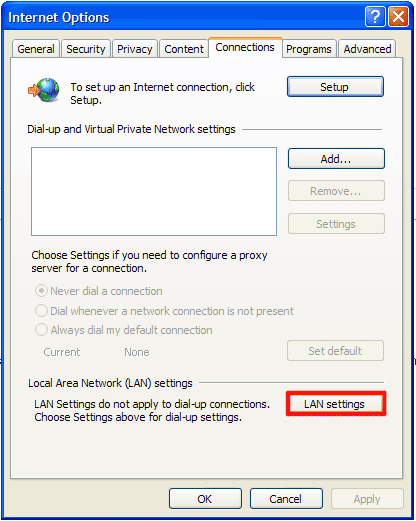
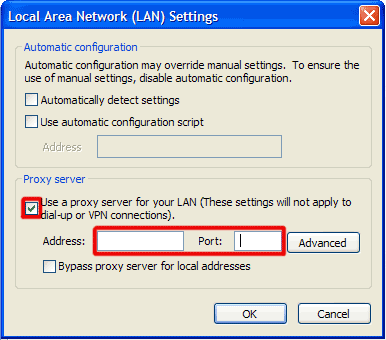
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Secure Web Patch
| ||||||||

|
How to manually remove Windows Secure Web Patch
Files associated with Windows Secure Web Patch infection:
%AppData%\Protector-[Random].exe
%AppData%\result.db
%AppData%\1st$0l3th1s.cnf
%CommonStartMenu%\Programs\Windows Secure Web Patch.lnk
%Desktop%\Windows Secure Web Patch.lnk
Windows Secure Web Patch DLL's to remove:
Windows Secure Web Patch processes to kill:
Remove Windows Secure Web Patch registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "otbpxlqhjd"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmdagent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[1].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npfmessenger.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsadbot.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe

Post comment — WE NEED YOUR OPINION!