- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Shows commercial adverts
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Turnkey ConsoleWindows Turnkey Console is one more cunning application, filling the ranks of the vast Rogue.VirusDoctor group, which has produced such dangerous, rogue applications as Windows Malware Firewall, Windows Antivirus Rampart and Windows Ultimate Security Patch. Be sure that the fake security tool will be used by cyber crooks to fool you and gather unlawful profits from you, all of which is enabled by the rogue’s pretentious exterior. Since the vicious program attacks Windows systems only, its layout resembles one of the regular Windows programs, and various elements, attributed to legal antimalware applications, can be noticed. Such elements include Firewall, Automatic Updates, Antivirus protection or Anti-Phishing, all of which could help you detect, delete or guard-against malware! However, these are just a bait to make you believe the fictitious security application, and you should hurry up to delete Windows Turnkey Console from your system right away. First of all, be extremely aware of the fictitious security notifications, which you will not be able to remove, and which will keep recommending you to purchase Windows Turnkey Console’s malware removal version: Warning! Spambot detected! Error Recommended: Once you notice such bogus alerts, and the fake computer scanner falsely informs you of fictitious computer threats, beware of other Windows system symptoms, which should make you believe the infection, and which should stop you from having Windows Turnkey Console removed. Amongst such malfunctions, blocked Internet connection, removed access to Registry Editor, Task Manager, and disabled running of most Windows executable files are the most important, because without these controls, you will not be able to delete Windows Turnkey Console quickly. Having the malicious program removed from your system is, unfortunately, much more difficult than you can expect, and we recommend starting with a simple activation key, which will help you restore Windows functionality: 0W000-000B0-00T00-E0020. And to regain internet connection, you can also follow the guidelines of the connection renewal instructions we have produced for you. With the ability to access Task Manager and Registry Editor you will be able to delete Windows Turnkey Console manually, if you have previous experience, and restored ability to connect to the web will allow you to install automatic malware removal tools. The later should be your most valued option, because with legitimate security applications guarding your Windows system, all malicious programs will be detected and deleted quickly!
Download Spyware Removal Tool to Remove* Windows Turnkey Console
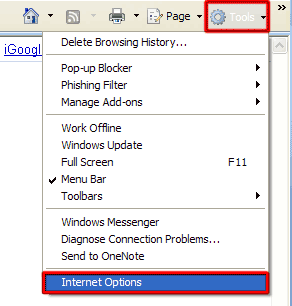
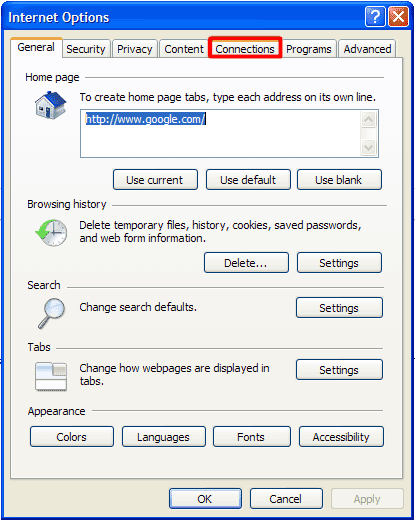
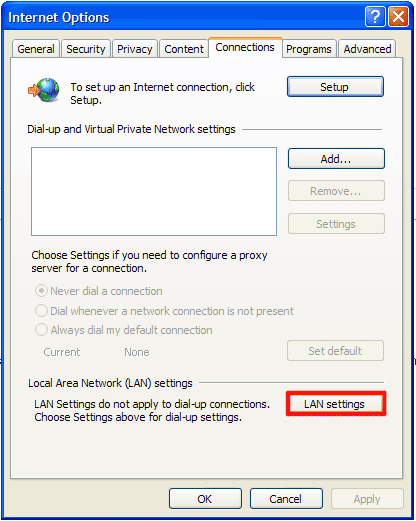
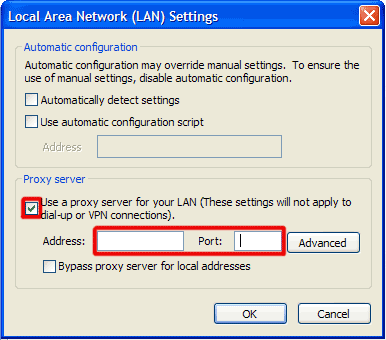
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Turnkey Console
| ||||||||

|
How to manually remove Windows Turnkey Console
Files associated with Windows Turnkey Console infection:
%AppData%\Protector[Random].exe
%AppData%\result.db
%Desktop%\Windows Turnkey Console.lnk
Windows Turnkey Console DLL's to remove:
Windows Turnkey Console processes to kill:
Remove Windows Turnkey Console registry entries:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsavastsvc.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsavastui.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsegui.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsekrn.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsmsascui.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsmsmpeng.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsmsseces.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionSystemRestore "DisableSR " = '1'

Post comment — WE NEED YOUR OPINION!