- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Slow internet connection
- Annoying Pop-up's
- Slow Computer
Windows Defence CounselDo not wait until cyber crooks steal your money. Remove Windows Defence Counsel because it is a phony security tool which aims to commit identity theft. Do not enter your credit card number and passwords in a purchase form of the rogue because the information that you reveal is recorded by the criminals. Windows Defence Counsel is ascribed to the Rogue.VirusDoctor family which also includes such malicious software as Windows Pro Safety, Windows Private Shield and a bunch of rogues of the same kind. None of them can be trusted, and if you find any of the malware mentioned, do not delay to remove it from the system. You will notice how diligently the malware “protects” your system, or rather informs about potential threats. Windows Defence Counsel displays bogus infections which might be widely known as Trojans or worms, but in the case of the infection of this threat, the names of authentic Trojans do not mean anything. The rogue also simulates pop-ups, which appears in Task Bar. You might receive bogus notifications saying that some infections have been detected or that you have to activate this malware so that the infections are removed. Here are some examples of how you might be tricked by Windows Defence Counsel: Error Error It is important that you ignore these notifications, because if you follow the instruction to activate Windows Defence Counsel, you will be asked to enter your financial information. Bear in mind that such system’s impairments as disabled Internet, Registry Editor and Task Managers are produced by Windows Defence Counsel. The Internet is vital to download a removal tool; Registry Editor is necessary to locate and delete registry entries created by the rogue. Task Manager is disabled in order to hide the malicious processes and to prevent the removal of Windows Defence Counsel. Furthermore, security applications are terminated. Do not wait and delete Windows Defence Counsel. Read on if you want to know how you can get rid of the rogue. In order to terminate the infection, you have to restore your Registry Editor. When it is recovered, you will be able to access the Registry and remove the malicious entries. For this, you have to activate the Windows Defence Counsel so that it starts running as if it was registered after the purchase of the fake full version. Furthermore, enter an activation key 0W000-000B0-00T00-E0020 and start removing the rogue. If you find the removal too confusing, delete Windows Defence Counsel automatically. For the automatic removal, should use a legitimate antispyware program, which ensures that the infection is fully deleted. It is essential that the rogue be removed without any components left in the system, and in this case, legitimate antispyware is the best option.
Download Spyware Removal Tool to Remove* Windows Defence Counsel
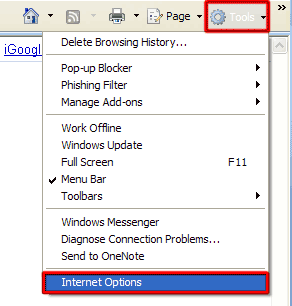
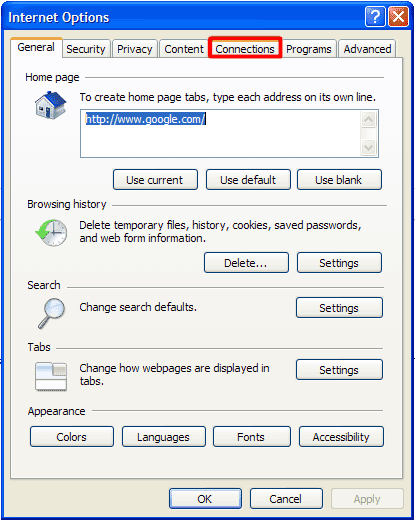
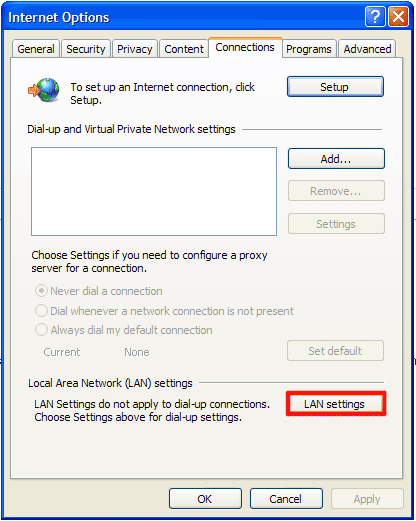
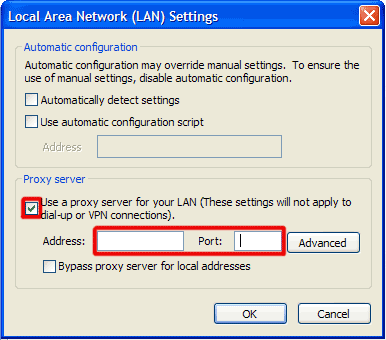
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Defence Counsel
| ||||||||

|
How to manually remove Windows Defence Counsel
Files associated with Windows Defence Counsel infection:
Protector-myww.exe
Protector-ogon.exe
%AppData%\result.db
%AppData%\Protector-[Random].exe
%AppData%\NPSWF32.dll
Windows Defence Counsel DLL's to remove:
Windows Defence Counsel processes to kill:
Protector-ogon.exe
%AppData%\Protector-[Random].exe
Remove Windows Defence Counsel registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-5-27_7"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "whecqycyiq"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ackwin32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\adaware.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BDSurvey.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fsm32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\infwin.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pavsched.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sbserv.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ssg_4104.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\webdav.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zapro.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0
_HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ERROR_PAGE_BYPASS_ZONE_CHECK_FOR_HTTPS_KB954312

Post comment — WE NEED YOUR OPINION!