- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Normal system programs crash immediatelly
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Advanced User PatchThere are many security applications out there trying to sell their products; however, some of them, just like Windows Advanced User Patch, may be completely fake and should be ignored completely. Unfortunately, such fictitious programs are usually camouflaged to be infiltrated into Windows systems, and can come in with bundled downloads, through spam email attachments, fake online scanners or black hat SEO scams. And it might be harder than you think to remove Windows Advanced User Patch from your computer, once it settles in. This task may not be easily manageable, because with Windows Advanced User Patch existence in your PC, there may be some Windows system malfunctioning happening. What is worst, Windows Advanced User Patch’s RUN key will be added to your system’s start-up, to make the malicious infection’s processes run immediately after PC’s launch. One more thing you will not be able to miss will be Windows Advanced User Patch computer scanner and pop-up notifications, flooding your screen. Moreover, you will not be able to remove reappearing infection’s interface windows and notifications, until you delete Windows Advanced User Patch from your system. If you leave Windows Advanced User Patch running in your personal computer, the rogue might open up backdoors to more high-risk malware, and if you pay money for Windows Advanced User Patch’s licensed version, you might put your sensitive data at risk. Obviously, there is no way out but to delete Windows Advanced User Patch as fast as possible! Do so manually, if you have previous experience, or trust automatic option, by installing legal tools. Most importantly, remember that you should still worry about infection’s removal, even if you have paid for its licensed version, and various Windows symptoms, seem to have disappeared from your PC. There is no way to tell, whether Windows Advanced User Patch will not strike again, if you keep its malignant files in your system’s background! UPDATEIf you are to delete Windows Advanced User Patch you might as well use the same tactics that has been applied to previous versions of this rogue including Windows Safety Module, Windows High-End Protection, Windows Recovery Series and many more. Since all rogues from Rogue.VirusDoctor family that have been released recently are more or less identical, they can be all removed in a similar way. As far as Windows Advanced User Patch is concerned, you will definitely find this activation key useful: 0W000-000B0-00T00-E0020 It was mentioned already that Windows Advanced User Path wants you to register it, otherwise it will not "remove" the malware. With this code you can "register Windows Advanced User Patch after having clicked the "Activate Ultimate Protection" button, but rather than activating the rogue itself, the code will help you to remove Windows Advanced User Patch from your computer. That is so, because activation subdues the infection's symptoms. Windows Advanced User Patch has a disturbing ability of blocking executables, Internet browser, Windows Task Manager and Registry Editor, making it basically impossible to delete it without outside help. On top of that, if turning your computer into a vegetable weren't enough, Windows Advanced User Patch also displays the following security messages that are obvious lies: Warning Error Warning Therefore, the moment you "activate" the rogue, do not wait any longer and acquire a legitimate security tool that will help you to erase Windows Advanced User Patch for good. You can also try removing Windows Advanced User Patch manually, but that is not recommended unless you are an experienced computer user.
Download Spyware Removal Tool to Remove* Windows Advanced User Patch
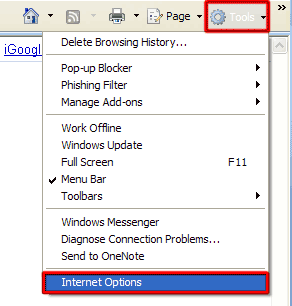
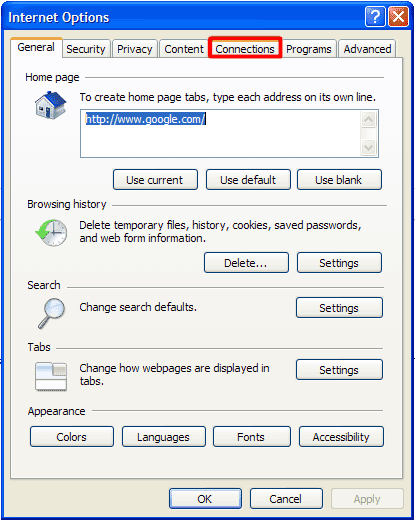
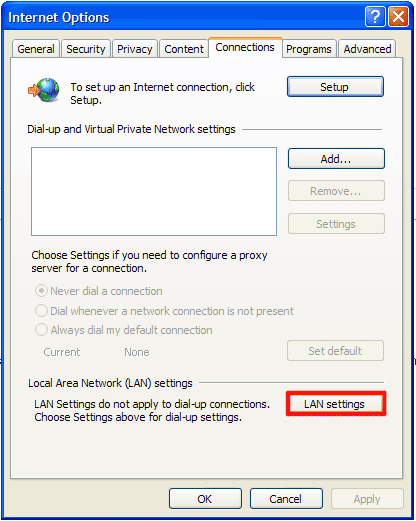
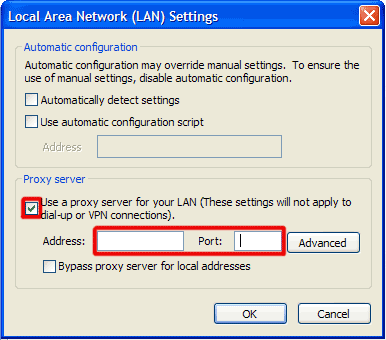
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Advanced User Patch
| ||||||||

|
How to manually remove Windows Advanced User Patch
Files associated with Windows Advanced User Patch infection:
%CommonStartMenu%\Programs\Windows Advanced User Patch.lnk
%AppData%\result.db
%AppData%\W34r34mt5h21ef.dat
%AppData%\Protector-[Random].exe
%AppData%\NPSWF32.dll
Windows Advanced User Patch DLL's to remove:
Windows Advanced User Patch processes to kill:
Remove Windows Advanced User Patch registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-5-6_2"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "ungklgkqft"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alertsvc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\belt.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\iface.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\netspyhunter-1.2.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rscdwld.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tcm.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winstart.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0

Post comment — WE NEED YOUR OPINION!