- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows High-end ProtectionThe makers of Windows High-End Protector did a decent job because they made a counterfeit application which looks like a legitimate Windows security program. This rogue belongs to the Rogue.Virus Doctor family which includes such malware as Windows Recovery Series and Windows Safety Checkpoint, which look identical. On the interface of Windows High-End Protector, you will find the same colors and icons which are found in your OS. This feature is one of a few characteristics of Windows High-End Protector making you think that this malware should not be removed from the system. Other characteristics of Windows High-End Protector’s performance are so believable that a Windows user might start thinking that he or she is using a legitimate security application. For instance, the task bar will display bogus pop-ups saying that your system is at risk. Moreover, Windows High-End Protector obsessively “scans” the systems and then displays a bunch of imaginary threats. As this malware does not scan your computer, the content of the messages should not be trusted. You might find a notification ant the bottom of the scan table: Recommended: Do not follow this instruction because you will be asked to purchase a full version of the rogue. Those fake notifications cannot be disabled through any settings. Only a registration key, which is provided by Windows High-End Protector after the purchase of its fake full version, can help you in this case. You do not have to make any purchase because the key is given for you. The key also allows users to remove the rogue manually: Registration key: 0W000-000B0-00T00-E0020 Not only does the registration key disable annoying pop-ups, it also restores the access to certain processes which become unavailable to reach after Windows High-End Protector is installed. It will restore Internet connection, Registry Editor, Task Manager and executes which would automatically detect and delete Windows High-End Protector for you. This registration key is a “life buoy” in this uncomfortable situation, when you want to remove Windows High-End Protector manually. Although you can choose from the manual and automatic removal of Windows High-End Protector, the first way of removal is not an easy process. The manual deletion of the rogue means that you have to get rid of all the malicious components of the malware in order to prevent its regeneration. Do not undertake this task if you do not know how to start the procedure. The best way to remove Windows High-End Protector and clean your system is to install a legitimate antispyware tool. It will scan all parts of the systems and delete Windows High-End Protector.
Download Spyware Removal Tool to Remove* Windows High-end Protection
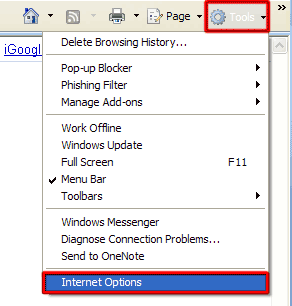
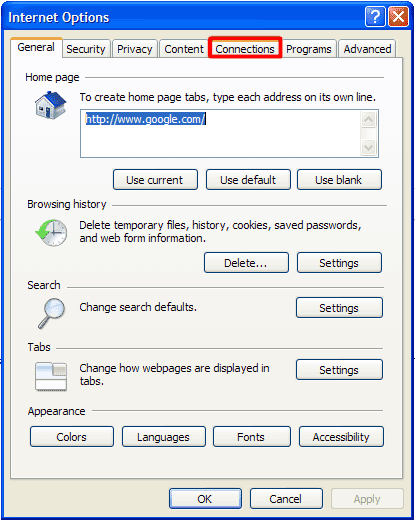
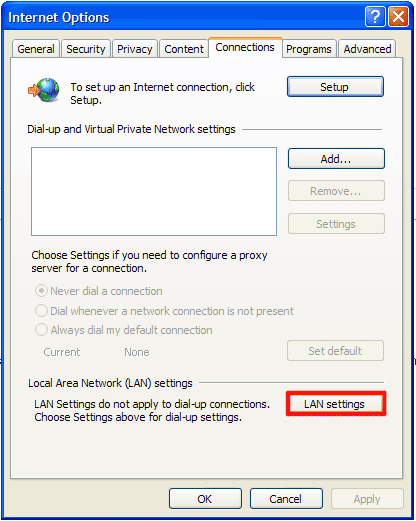
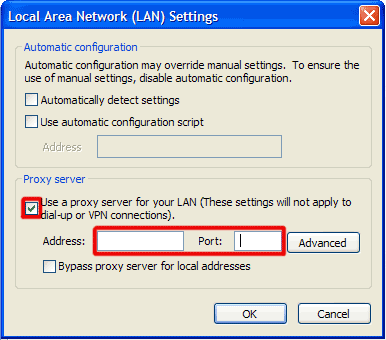
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows High-end Protection
| ||||||||

|
How to manually remove Windows High-end Protection
Files associated with Windows High-end Protection infection:
%AppData%\Protector-[Random].exe
%AppData%\result.db
%CommonStartMenu%\Programs\Windows Antivirus Care.lnk
%Desktop%\Windows Antivirus Care.lnk
Windows High-end Protection DLL's to remove:
Windows High-end Protection processes to kill:
Remove Windows High-end Protection registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "okanrqfdwk"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atro55en.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bisp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\esafe.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[4].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mssmmc32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pcip10117_0.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\scrscan.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utpost.exe

Post comment — WE NEED YOUR OPINION!