- Blocks internet connection
- Block exe files from running
- Connects to the internet without permission
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Component ProtectorThe Rogue.VirusDoctor family reproduces its “members” day by day and its latest production is Windows Component Protector which is a clone of Windows Cleaning Tools, Windows Care Taker and other malicious software. Windows Component Protector should be removed from the system as soon as it informs users about its presence. This bogus application does not make diagnosis of the system’s security and does not aim to help you with deletion of the supposedly found threats. The aim of this malware is to convince you to pay money for an imaginary application and to expose your credit card numbers, passwords and any other financial information to cyber crooks. Your aim, in return, is to remove Windows Component Protector from your computer. The cyber criminals who created Windows Component Protected wanted to make it look as convincing as possible which would ensure that the rogue will stay in the system and will not be removed. Judging from the outside, the interface of the malware looks similar to any legitimate Windows table but the truth is that it should not be trusted at all. Fake check ups, misleading result and fake warning should not be trusted as well. We present some examples of the notifications and messages that might be displayed by Windows Component Protector: Warning Error Error However, these fake messages are nothing compared to other tricks. Windows Component Protector tries to deceive users by disabling execution of certain parts of the system. For instance, Registry Editor and Task Manager are disabled so that users cannot control the system’s processing. Moreover, some executes are blocked which helps the rogue to stop the system from running security scans so that the rogue would be detected. In addition, Windows Component Protector disables access to the Internet and users cannot find out how to solve the problem. The solution that is given to them is a purchase of the malware which actually does not solve the problem but makes more trouble. Do not make any money transfers, and do not reveal your financial information on the purchase page because this is all the criminals need. The only way to set everything in order is to remove Windows Component Protector from the system. To facilitate the process of deletion, use a registration code which will restore the Mask Manager, access to the Internet and will disable annoying pop-ups: Registration code: 0W000-000B0-00T00-E0020 When you enter the code, the next step of yours should be finding a legitimate antispyware tool which will delete all malicious files of the rogue. It is essential to remove all files related to Windows Component Protector because if any hazardous component is left, the system might get infected by the same or a different infection. This is the reason why we do not suggest you remove the rogue manually but use a registered tool which will solve the problem and will not cause serious damage to the system.
Download Spyware Removal Tool to Remove* Windows Component Protector
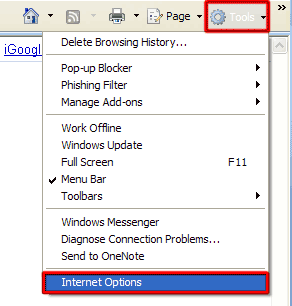
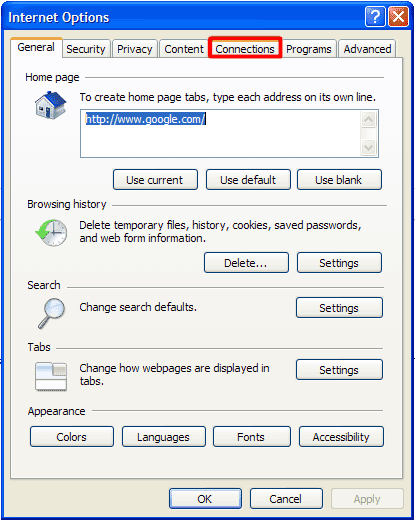
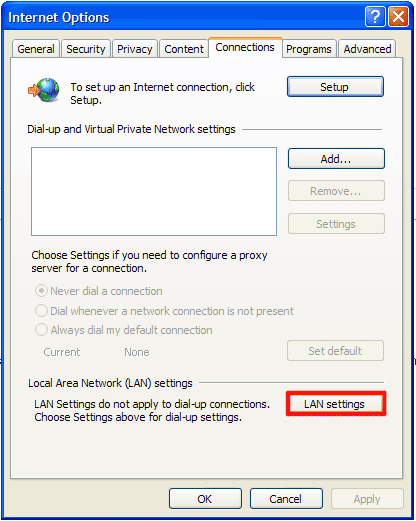
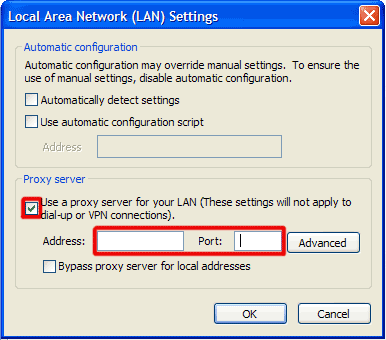
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Component Protector
| ||||||||

|
How to manually remove Windows Component Protector
Files associated with Windows Component Protector infection:
%AppData%\Protector-[Random].exe
%AppData%\result.db
%CommonStartMenu%\Programs\Windows Component Protector.lnk
%Desktop%\Windows Component Protector.lnk
Windows Component Protector DLL's to remove:
Windows Component Protector processes to kill:
Remove Windows Component Protector registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "okanrqfdwk"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atro55en.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bisp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\esafe.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[4].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mssmmc32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pcip10117_0.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\scrscan.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utp

Post comment — WE NEED YOUR OPINION!