- Blocks internet connection
- Block exe files from running
- Connects to the internet without permission
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Cleaning ToolsWindows Cleaning Tools is a fake security program which belongs to the same Rogue.VirusDoctor family as Windows Stability Maximizer, Windows Processes Accelerator and many other rogues which are created to trick people into buying fake security programs. As its predecessors, Windows Cleaning Tools should be removed from the computer because once it is installed, it aims to commit a financial data theft and to rip users off. Ignore all fake information presented by Windows Cleaning Tools and be ready to dispose of this malware. Windows Cleaning Tools applies different acts of intimidation to make gullible users think that their computer is under threat. For example, the system is supposedly scanned and imaginary threats are presented as such real infections as Trojans or viruses. To build more tension, constant and annoying pop-ups appear in a screen. To exemplify how the rogue threatens Windows users, some of the fake notifications are presented below. If you find anything like this displayed by Windows Cleaning Tools, remember that it is not worth paying attention to imaginary alert messages. Error Warning The rogue also blocks Internet access and users cannot find relevant online information about the Windows Cleaning Tools and its removal. In this way the rogue is trying to suspend its removal for as long period of time as possible. However, there is away to access the Internet which is either to run the system in Safe Mode with networking and to download an antispyware tool, or to use friends’ computer in order to get all necessary tools. In addition, Windows Cleaning Tools does not allow the system to run some executes which is done to prevent the malware from detection. The longer this bogus application resides in the system, the bigger impact on users is achieved. The Windows Task Manager and Registry Editor are also disabled, and in this way Windows users are no longer in control of the system. All these factors discussed above might frighten users to such an extent that they decide to pay money for fake malware and that is how their money, credit card number and passwords are exposed to cyber criminals. The purchase of the malware will not help get rid of fake application; however, a registration key, which is usually provided for users after the purchase, will help disable annoying pop-ups which will ease up the procedure of the rogue’s deletion. Keep in mind, that the removal of Windows Cleaning Tools is a must if you want to protect your system. Registration key: 0W000-000B0-00T00-E0020 When you enter the code, you can start thinking how you are going to get rid of the rogue. Remove Windows Clean Tools either manually or automatically. As manual removal is not for every Windows user, consider if you are capable of deleting all malicious components from the system. If you already find it difficult, we recommend using a legitimate antispyware tool which will detect the rogue and remove it from the system.
Download Spyware Removal Tool to Remove* Windows Cleaning Tools
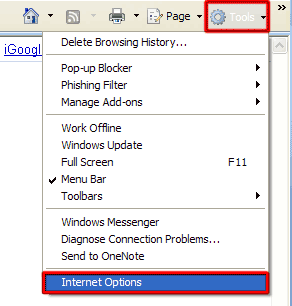
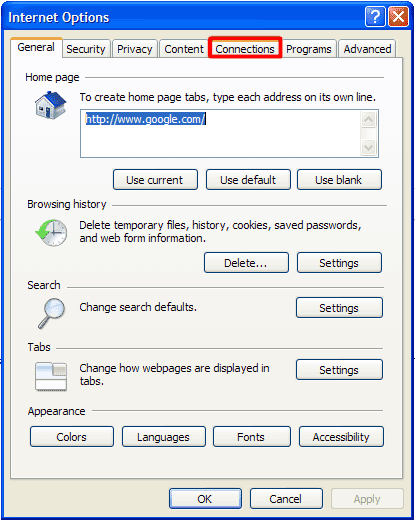
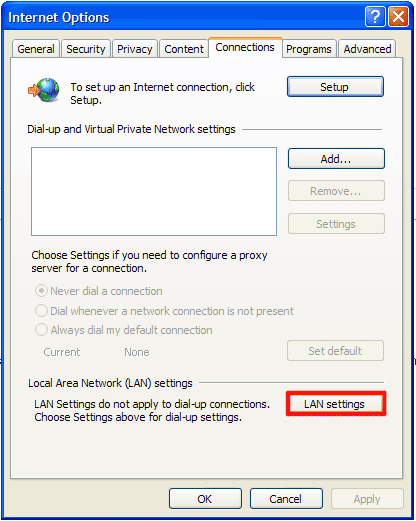
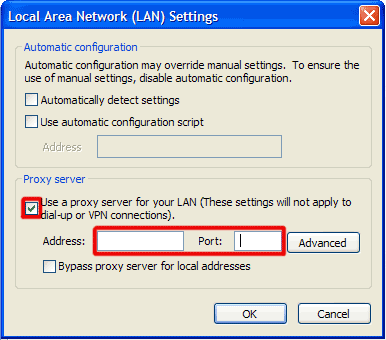
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Cleaning Tools
| ||||||||

|
How to manually remove Windows Cleaning Tools
Files associated with Windows Cleaning Tools infection:
%AppData%\Protector-[Random].exe
%AppData%\result.db
%CommonStartMenu%\Programs\Windows Cleaning Tools.lnk
%Desktop%\Windows Cleaning Tools.lnk
Windows Cleaning Tools DLL's to remove:
Windows Cleaning Tools processes to kill:
Remove Windows Cleaning Tools registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "okanrqfdwk"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atro55en.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bisp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\esafe.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[4].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mssmmc32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pcip10117_0.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\scrscan.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utp

Post comment — WE NEED YOUR OPINION!